A user of a software system published by a third party for which we are the developer experienced an error message today indicating that a Codebase file used by the system was corrupt (in this case, the error was a -70 status on FILELOC.DBF, a file that our runtime executable opens on startup).
It is normally very unusual for this file to become corrupted through normal operation; it is even more unusual in this particular vertical software system since it is opened but never updated (i.e. written to).
Without seeing the system, initially we could only assume that the file probably had a bad index and needed to be rebuilt. After going through those steps with our customer contact and discussing the need to first make a backup of the file before attempting the rebuild and also ensuring that users had exited the software, we then received a phone call indicating that while viewing the folder containing the system files including the location of the FILELOC.DBF file, he was seeing some very strange long file names with ".locky" file extensions. We were then able to access the system, and this is what we saw:
 |
| Locky virus infestation |
Realizing that the corruption of the file was in fact being caused by ransomware encryption, we terminated the remote access and advised the user to immediately contact their IT support staff.
The LOCKY ransomware virus can apparently spread via network shares without requiring mapped network drives. So relying on non-mapped drives will not be an effective strategy to deter its spread. In this case, an e-mail was opened from a laptop client and the virus quickly (probably within minutes) spread to the file server via a standard UNC share (the folder above is a server folder view; the e-mail infection was not however originated from the server).
We note this March 16, 2016 report from a hospital in Kentucky similarly infected:
Hospital Declares ‘Internal State of Emergency’ After Ransomware Infection
Some helpful background on this virus is available here:
New Crypto-Ransomware Locky Uses Malicious Word Macros (Trend Micro 2/19/16)
“Locky” ransomware – what you need to know (Sophos 2/17/16)
Locky malware, lucky to avoid it (Microsoft Malware Protection Center 2/24/16 blog)
Remove Locky Ransomware and Restore .locky Encrypted Files (SensorsTechForum 2/16/16)
Blocking the Locky Ransomware Virus - Update and Tips (GreenviewData 2/25/16)
As the Microsoft blog notes, the virus is being spread in a familiar way via e-mail spam (the Trend Micro report indicates that it is disguised as an innocuous e-mail with changing headers referring to the attachment of a fake invoice contained in a Word document). The virus reportedly can be activated by simply opening the e-mail (i.e. can be contained in the body of an e-mail) and not just by opening the attachment, although, that seems somewhat unlikely since the script that causes the infection is via a Word macro.
As with CryptoLocker ransomware that we wrote about on October 15, 2014, end user education is again paramount to avoid being infected. There are indications that the virus can be triggered simply by opening up an e-mail (probably via an embedded link in an HTML-based e-mail). So we would recommend not even opening an e-mail from either a suspicious or non-trusted source. To say another way, you may be able to become infected not only by opening a file attachment, but also even by simply opening the e-mail itself. Mail programs that provide an initial preview without opening the incoming mail are still likely safe.
Users should be instructed never to affirmatively respond to a query asking them to enable scripting of any kind. Traditional anti-virus software approaches are not enough; just because your anti-virus definitions are current does not mean that you are protected.
The need to keep frequent backups also cannot be emphasized enough should an infection occur. In this situation, the user had a backup that was only two hours old and therefore was able to almost completely recover (there were still seven corrupted files in the software system that we support that we were able to simply replace; eventually the virus would have encrypted everything, but for whatever reason decided to encrypt files with a DBF extension first, probably recognizing them as a well-known data file type). The Codebase error returned on all seven files was a -200 which translates to "File is not a data file."
In addition you can take some steps as outlined in the links above that will help to avoid malicious scripts from being run.
Sample screen shots of some of the screen settings to consider for Adobe Reader, Fox Reader, and OpenOffice are contained below. For Microsofit Word/Excel macro security settings, see the Microsoft Malware Protection Center blog link above.
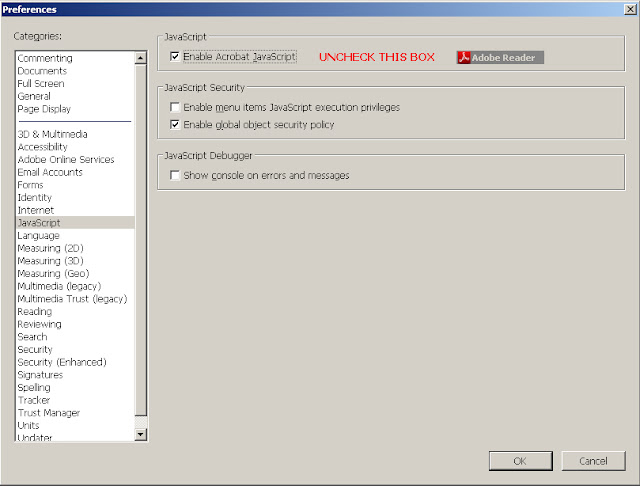 |
| Disabling JavaScript in Adobe Reader Acccess via Edit --> Preferences from the reader menu |
More re: Adobe Reader:
Under "Trust Manager" you may also want to uncheck "Allow opening of non-PDF file attachments with external applications."
And, under "Security (Enhanced)" you may want to uncheck "Automatically trust sites from my Win OS security zones."
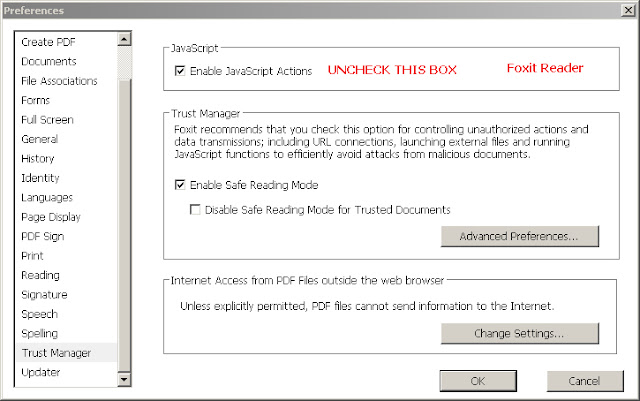 |
| Disabling JavaScript in Foxit Reader Access via File --> Preferences Verify that enable safe reading mode is checked |
Under "General" you may also want to uncheck "Create links from URLs."
 |
| OpenOffice Step #1 From Tools --> Options while in any of the program options |
 |
| OpenOffice Step #2 Raise the security level to very high |
